“In the space of one hour, my entire digital life was destroyed. First my Google account was taken over, then deleted. Next my Twitter account was compromised, and used as a platform to broadcast racist and homophobic messages. And worst of all, my AppleID account was broken into, and my hackers used it to remotely erase all of the data on my iPhone, iPad, and MacBook.
In many ways, this was all my fault. My accounts were daisy-chained together. Getting into Amazon let my hackers get into my Apple ID account, which helped them get into Gmail, which gave them access to Twitter. Had I used two-factor authentication for my Google account, it’s possible that none of this would have happened…“
source: How Apple and Amazon Security Flaws Led to My Epic Hacking
2-factor authentication goes by various names including:
- Two-factor authentication (of course!)
- 2-step authentication
- Multi-factor authentication. OK, multi-factor authentication could involve 3 or 4+ steps, but the principal is the same. This movie clip shows a fantastic example of multi-factor biometric authentication 😀
https://www.youtube.com/watch?v=lI6Ci-fkFtA
So the words ‘authentication’ and ‘verification’ are interchangeable, as are ‘factor’ and ‘step’.
It’s a very easy concept, wrapped up in big words. All it means is that you’ve got to provide more than just one method of verification (such as a password) to successfully access something, but typically a computer system such as online banking.
By having to provide more than a single method of verification, you’ve sacrificed a little bit of time & convenience for exponentially greater security. Which makes 2-factor authentication a very, very good thing to be taking advantage of whenever you’re offered the opportunity. (authors note: I use 2-factor authentication for approximately 10 different systems at time of writing, and I want that to rise).
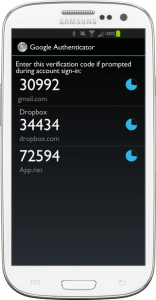
The most common forms of providing a second method of authentication are:
- Using a smartphone app to generate new passwords for you that change every 30 seconds or so. Such passwords are also known as one-time passwords. One such app is called Google Authenticator (see Samsung smartphone image to the right) and is available for Android, iOS and Blackberry. Don’t think that just because it’s a Google app it’s therefore biased towards Google devices or systems. Quite the opposite. Any computer system can choose to use it – or other similar apps – to provide one-time passwords for users of their systems.
- A physical device such a security token or dongle that your bank might provide and that can hang on your keyring – see image below-right (the RSA SecureID). Such devices offer exactly the same service as your Google Authenticator app, except that they’re typically limited to providing security for just a single system – so less versatile. You certainly wouldn’t want to be carrying 10 different dongles on your keyring for 10 different systems.
- Good old fashioned SMS. When you try to login to a system (or indeed perform a significant event inside a system such as a money transfer from your bank account), it sends an SMS to your phone (smart or otherwise!) that you must first enter before the transaction will complete.
- Biometric security, such as a fingerprint or eye (iris or retina) scan. In other words, any method that is able to distinguish you from anyone else on the planet with a sufficient degree of confidence. It’s quite amazing how many biometric opportunities there are.
- Not necessarily to be used only in a 2-factor authentication scenario, but this use of NFC technology looks very interesting: the NFC Ring. For example, imagine that the only person who can use your mobile phone is the person (hopefully you!) who is wearing the NFC ring that has been ‘paired’ with your phone. Just don’t hold your phone in the wrong hand!

You can expect to see more and more systems adopting some form of 2-factor authentication in the near future. It’s no wonder because all the signs are that, overall, cybercrime is on the rise, with no suggestion that it will ease off any time soon. The systems that adopt it first are typically ones that contain the most sensitive information and/or provide the most ‘power’ (such as funds transfer) to the authenticated user. But increasingly you’ll see less obviously confidential systems employ it – such as social media websites, CRM systems, etc. – simply because no-one likes having their data abused or stolen. Indeed, if you use a system that you consider to be confidential in nature that DOESN’T yet offer 2-factor authentication, we suggest you should demand it! For example, these increasingly disgruntled and shocked users of the very popular online accounting software Xero have been demanding it for over a year: Two Factor Authentication on Xero login.
No system is 100% secure in perpetuity. And 2-factor authentication is by no means the be-all and end-all of system security. But at time of writing it’s certainly one of the most potent, accessible, and relatively easy-to-use security methods out there.
How to find out if a system you use makes 2-factor authentication available? Google is your friend, e.g. here’s a search for Linkedin 2-factor authentication
Itomic’s recommendation: use 2-factor authentication at every available opportunity. The costs are hugely outweighed by the benefits.

